Preface
When you are full of confidence, the configuration of the packet capture environment is perfect, and you are ready to make a big fight. I found that a certain sound apk uses SSLPinning
When everyone confidently installed frida's SSLPinning and xposed's justtrustme on the phone, opened the apk again, and found that a certain sound apk used a non-system ssl library
The above is my experience. In order to avoid my detours, I will show you how to remove this sslpingng solution today.
Program
Open libsscronet.so of a certain tone, search for it, and then find it according to the keyword "SSL_CTX_set_custom_verify"
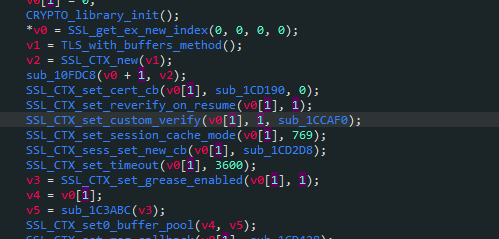
The third parameter is the place to check and is a callback function, so let's go in and see that
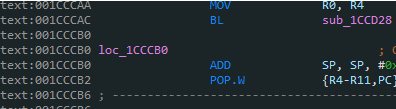
First find the place of ret, move the small hand and press the X key to find the reference and find one
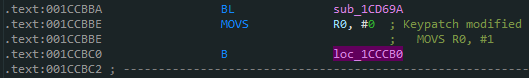
See that the return value is 1, but after checking and finding that the return value is 0, it is ssl_verify_ok
So we move the small hand and change it to 0, then there are 4 such points in total, save them all as 0 and save them
And then pulled out our beloved Android phone
adb shell
su
One operation to find the installation location of your own 17.3apk
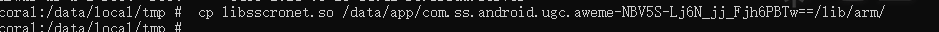
cp and then
chgrp system libsscronet.so
chown system libsscronet.so
chmod 777 libsscronet.so
Then open a certain sound and you will magically find that you can capture packets. In theory, all versions can be killed, as long as you find the keyword
If you don't want to use your hands to patch, here is a 32-bit version 17.3 so you can download and eat manually.
Remember the process, find a certain audio installation directory under your /data/data/, then cp into it, set a permission, and you can eat it happily

Post comment 取消回复