What is a JWT?
JWT, short for JSON Web Tokens, is a compact, URL-safe way to represent claims (information) to be transmitted between two parties, a client and a server. Think of it as a secret message in the form of a cryptographically signed note that only the intended recipient can understand
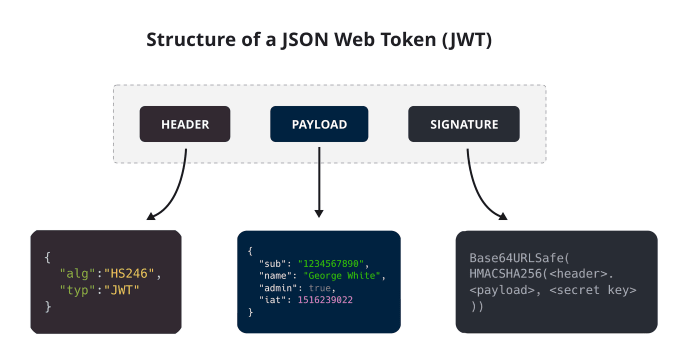
Structure of JWT
A JWT has three distinct parts, each separated by a dot (.):
- Header: Contains metadata about the token and the encryption algorithm used, usually HMAC SHA256 or RSA
- Payload: The actual data carried by the card is stored here. It is also known as "claims" and can contain data such as user details and other metadata
- Signature: Signature is a cryptographically secure proof that authenticates the sender and ensures that the message has not been altered in transit
How do JWTs work?
Here's a JWT in action:
- The client logs in with its credentials, and sends a request to the server.
- The server verifies these credentials. If they are valid, the server generates a JWT and sends it back to the client.
- The client typically stores the JWT in local storage and includes it in the headers of each subsequent HTTP request.
- The server validates the JWT after receiving these requests. If valid, the client is authenticated and authorized.
Why use JWT
JWTs are generic - any programming language can generate JWTs because they are JSON in nature. Also, they help maintain session state on the client side, reduce server load, and thus be more scalable
Security Considerations
While JWTs are convenient, they do have some vulnerabilities:
- Token theft: JWTs are stored on the client side and thus can be stolen. Always secure your transmissions, preferably over HTTPS.
- No built-in invalidation mechanism: Due to the stateless nature of JWTs, there is no way to invalidate JWTs individually or in groups of users.
- Token size: Storing too much data in a JWT can make it heavy, affecting network performance.
- Algorithm Vulnerabilities: Some algorithms in the JWT header are vulnerable. Always use a secure and updated algorithm and treat your signing key as a secret
In conclusion, JWT is a powerful tool in web development, providing stateless, secure and scalable communication. Keep in mind that the effective use of JWTs in your application depends on your specific needs and desired level of security
Post comment 取消回复