about post
poste is an open source mail service software, which can be easily built: SMTP + IMAP + POP3 + anti-spam + anti-virus + Web management + Web email, and supports the following features.
- Native implementation of SPF, DKIM, DMARC, SRS with simple wizard
- Antivirus engine ( ClamAV ) for detection of trojans, viruses, malware
- Built-in spam filter (RSPAMD)
- Webmail client (Roundcube) over HTTPS
- Email redirection, autoresponders and other filtering via Sieve scripting (email owner management, each action can be scripted)
- Quotas to limit mailbox space or number of emails
- System administrator, domain administrator, email owner have web management with different permissions.
- Built-in autodiscovery of Microsoft products, Thunderbird...
Diagnostics to help properly set up domains and mail servers - SMTP - port 25, 465 (TLS), 587
- POP3 - Port 110, 995 (TLS)
- IMAP - ports 143, 993 (TLS)
- SSL TLS Everywhere! No personal data, emails, logins are passed over the Internet unencrypted.
- By default, all passwords are stored as salted SHA512 hashes (5000 rounds). It will be very difficult for an attacker to crack your password.
- The entire mail server container is isolated from other applications by Docker.
Preparation
- One VPS with independent IP
- Support port 25 and email sending
- Recommended memory 2Gb or more
- Clean IP, not blocked, not marked as junk IP
- Install Docker in advance
Docker deployment poste
Docker deploys poste, which will hardly affect the existing services on your server. Copy the following command to execute
$ docker run -d \
-p 880:80 -p 8443:443 -p 25:25 -p 110:110 -p 143:143 -p 465:465 -p 587:587 -p 993:993 -p 995:995 -p 4190:4190 \
-e TZ=Asia/Shanghai \
-v /data/mail-data:/data \
--name "mailserver" \
-h "mail.your-domain.com" \
--restart=always \
-t analogic/poste.ioThe meaning of the parameters is as follows:
- 880/8443 is the WEB access port. In order to avoid conflicts with the local existing WEB services (nginx, etc.), 880/8443 is used here as the WEB port
- TZ=Asia/Shanghai: set the container to the Shanghai time zone
- /data/mail-data: Local data directory, modified to server directory according to actual situation
- mail.xxx.com: change to your own domain name
- --restart=always: Automatically restart when the container is abnormal
If the deployment encounters that port 25 is occupied, you can use netstat -apn|grep 25 to check whether it is caused by postfix. CentOS 7 can uninstall postfix:
$ yum -y remove postfixAfter deployment, visit https://IP:8443/ to complete the initialization settings according to the prompts
DNS settings
Go to the DNS service provider and set up domain name resolution according to the following requirements, otherwise the mail service cannot be used normally, among which:
- your-domain.com: for your own domain name
- 1.2.3.4: for your mail server IP
| Hostname | Record Type | Record Value |
|---|---|---|
| mail.your-domain.com | A | 1.2.3.4 |
| smtp.your-domain.com | CNAME | mail.your-domain.com |
| pop.your-domain.com | CNAME | mail.your-domain.com |
| imap.your-domain.com | CNAME | mail.your-domain.com |
| your-domain.com | MX | mail.your-domain.com |
| your-domain.com | txt | v=spf1 mx ~all |
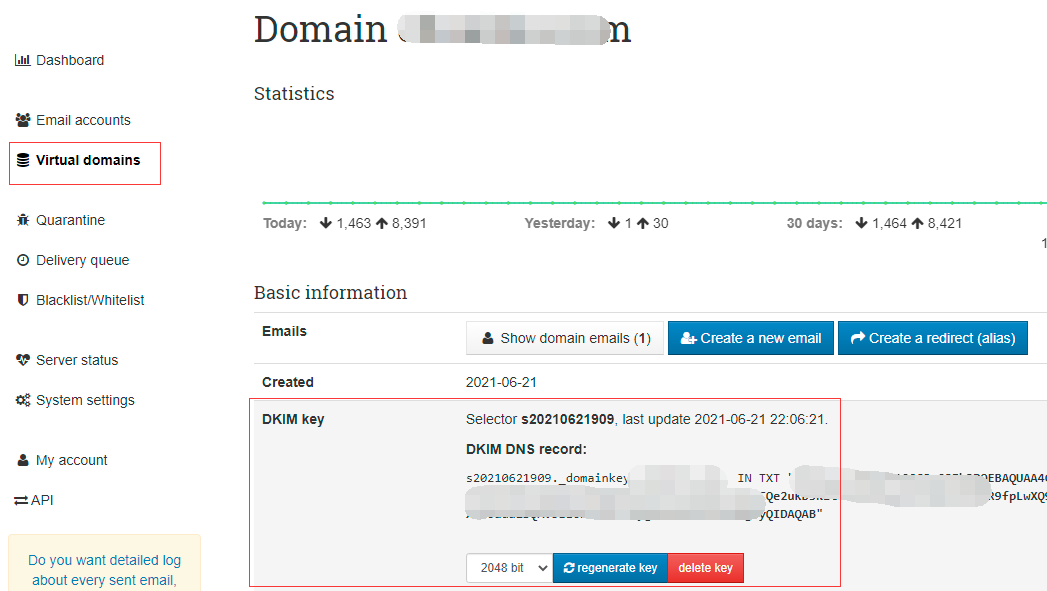
Set up DKIM verification
In the post background - Virtual domains - click on the corresponding domain name - DKIM key - create a key, and set the txt record resolution as required
Set PTR reverse analysis
PTR record is a kind of mail exchange record in email system; another mail exchange record is A record (in IPv4 protocol) or AAAA record (in IPv6 protocol). PTR records are often used for reverse address resolution
Domain name resolution to IP is called forward resolution, while IP pointing to domain name is called reverse resolution. Reverse resolution needs to be operated at the host service provider, please consult the host service provider for details.
For example, UltraVPS can directly add PTR reverse analysis in the background panel, and point the IP to your mail server, such as mail.your-domain.com
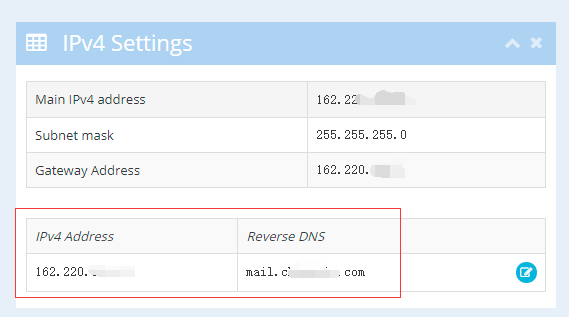
Adding SPF/DKIM/PTR analysis can improve the credibility of emails, thereby reducing the chance of emails entering the trash box, an essential key step
Set TLS SSL
After obtaining the SSL certificate, open the post background - System settings - TLS Certificate - select the certificate file to upload, see screenshot
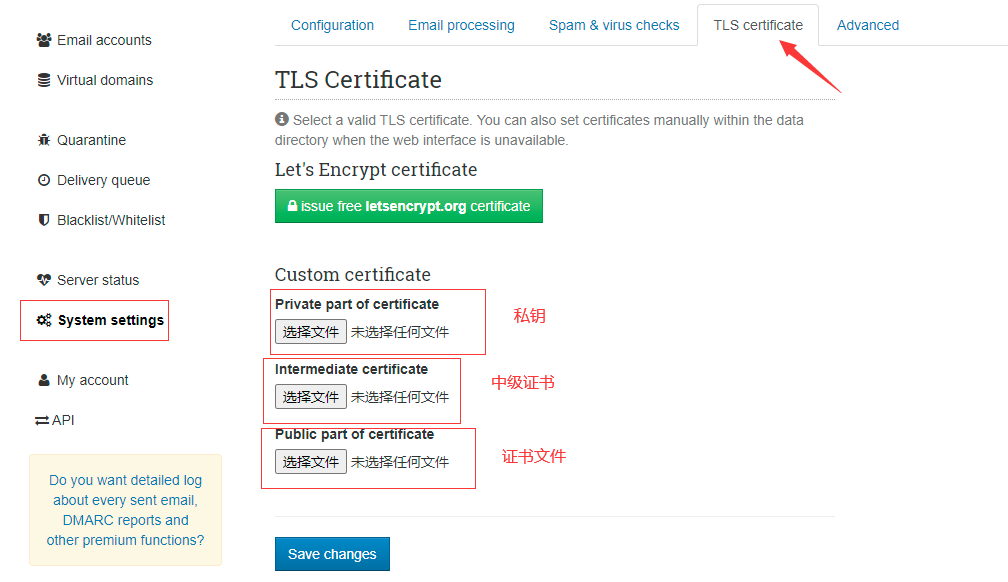
The SSL provider will automatically merge the intermediate certificate into the certificate file (such as Tencent Cloud), so the option of the intermediate certificate can be consistent with the certificate, and then click Save. After saving, you need to restart the container to take effect: docker restart mailserver
Login and Management
After enabling SSL, you can access it through the domain name: https://mail.your-domain.com:8443/, the default is to log in to webmail, and you can send and receive letters in webmail
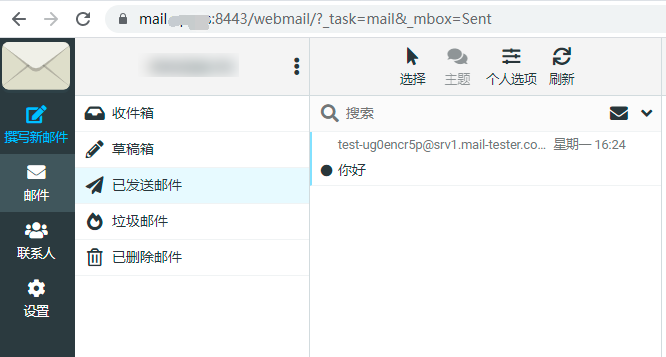
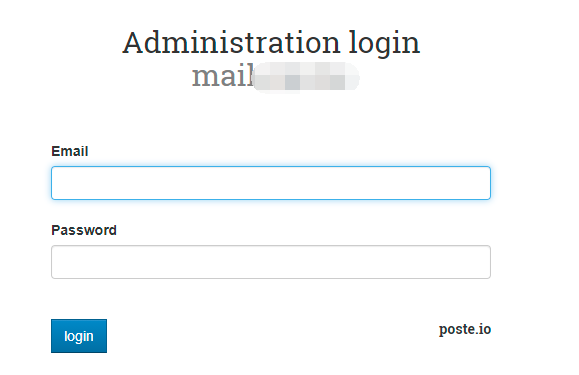
If you need to log in to the system management, you can change the address to https://mail.your-domain.com:8443/admin/login
Email benchmark test
You can use the tool https://www.mail-tester.com/ to run the email score, which will detect the problems in your email and give some optimization suggestions. Of course, the score of this tool is not absolutely accurate, the results are for reference only
suggestion
Before preparing to build your own email service, there are some precautions that need to be known. The following are some personal experience summaries, hoping to help
- Use highly credible domain name suffixes, such as .com/.net/.org, and try to avoid using all kinds of strange niche suffixes
- Use domain names with English letters, try to avoid using purely numeric domain names
- The longer the domain name registration time, the better, the minimum registration time is recommended to be longer than 7 days
- Use a clean IP, which can be queried through https://poste.io/dnsbl
- IP supports PTR reverse resolution, you need to consult the hosting company

Post comment 取消回复