Docker Daemon Socket TLS encryption
In order to prevent problems such as link hijacking and session hijacking from being attacked by an intermediary during Docker communication, both ends of c/s should communicate through encryption.
1. Create a folder and modify the host name (for subsequent use)
mkdir /tls
cd /tls
hostnamectl set-hostname server
bash2. Client operation
hostnamectl set-hostname client
vi /etc/hosts/etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.95.132 server3. Create ca secret key, set secret key password
openssl genrsa -aes256 -out ca-key.pem 4096
4. Create CA Certificate
openssl req -new -x509 -days 365 -key ca-key.pem -sha256 -out ca.pem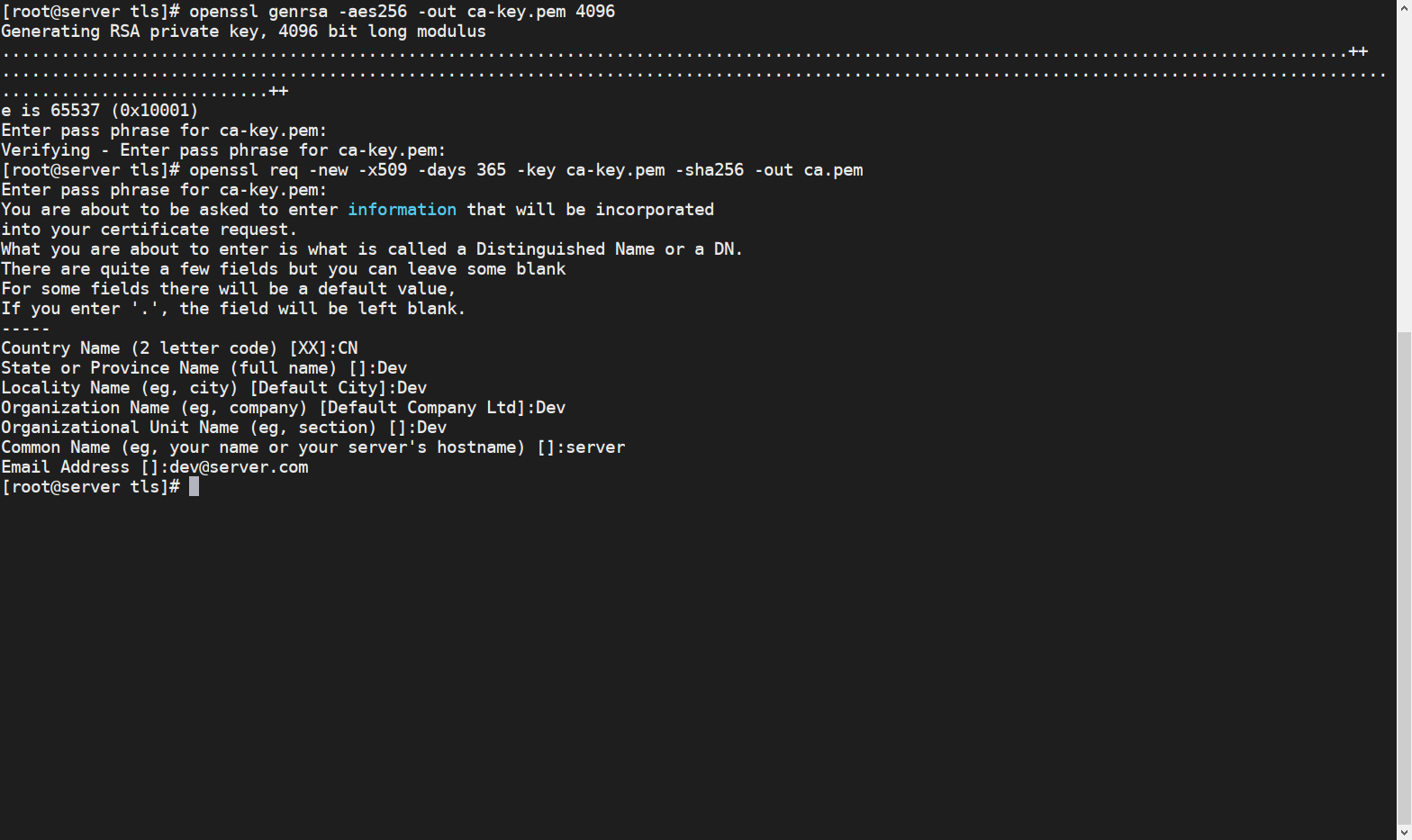
5. Create a server key
openssl genrsa -out server-key.pem 40966. Certificate Signing Request (CSR)
openssl req -subj "/CN=server" -sha256 -new -key server-key.pem -out server.csr7. Next, we will use our CA to sign the public key:
Since TLS connection can be established by IP address and DNS name, you need to specify the IP address when creating the certificate. For example, to allow the use of 192.168.95.133 (Client for testing) and connection to 127.0.0.1:
echo subjectAltName = DNS:server,IP:192.168.95.133,IP:127.0.0.1 >> extfile.cnfSet the extended use attribute of the Docker daemon key to be used only for server authentication:
echo extendedKeyUsage = serverAuth >> extfile.cnf8. Generate a signed certificate:
openssl x509 -req -days 365 -sha256 -in server.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out server-cert.pem -extfile extfile.cnf9. Generate client secret key
openssl genrsa -out key.pem 40969. Sign the client
openssl req -subj'/CN=client' -new -key key.pem -out client.csr10. Create a configuration file
echo extendedKeyUsage = clientAuth> extfile-client.cnf11. Generate a signed certificate
openssl x509 -req -days 365 -sha256 -in client.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out cert.pem -extfile extfile-client.cnf12. Modify the docker configuration file and restart the service
ExecStart=/usr/bin/dockerd --tlsverify --tlscacert=/tls/ca.pem --tlscert=/tls/server-cert.pem --tlskey=/tls/server-key.pem -H tcp:/ /0.0.0.0:2388systemctl daemon-reload
systemctl restart docker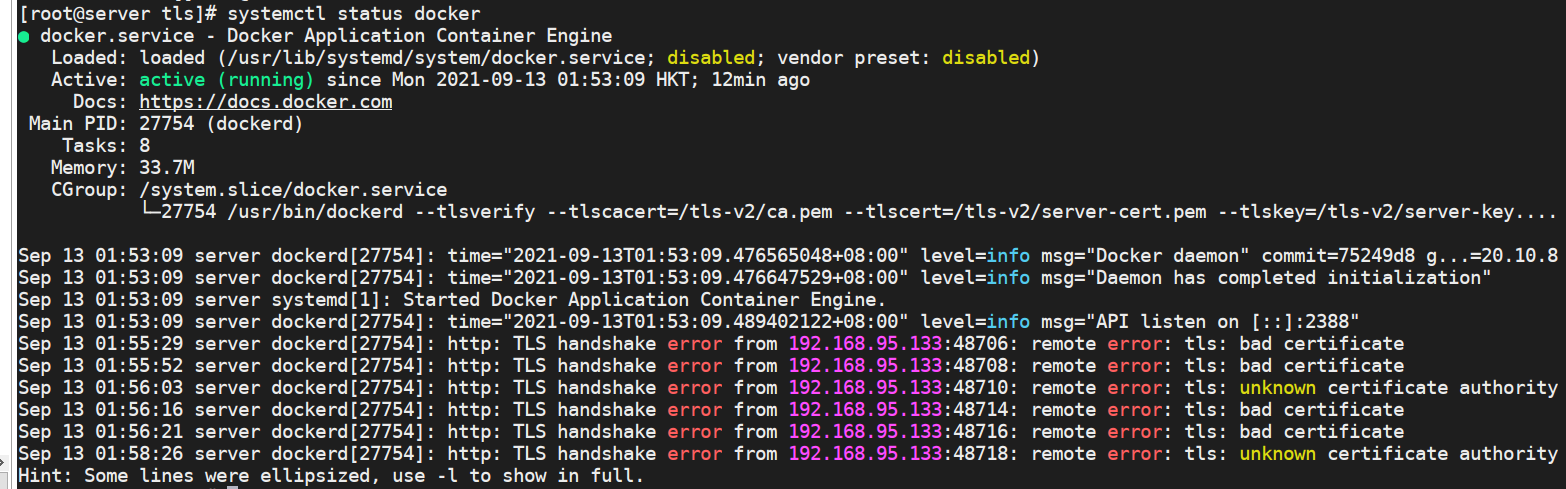
13. Copy the three files /tls/ca.pem /tls/cert.pem /tls/key.pem to the client's ~/.docker/
14. Server-side local verification
docker --tlsverify --tlscacert=/tls/ca.pem --tlscert=/tls/cert.pem --tlskey=/tls/key.pem -H=127.0.0.1:2388 version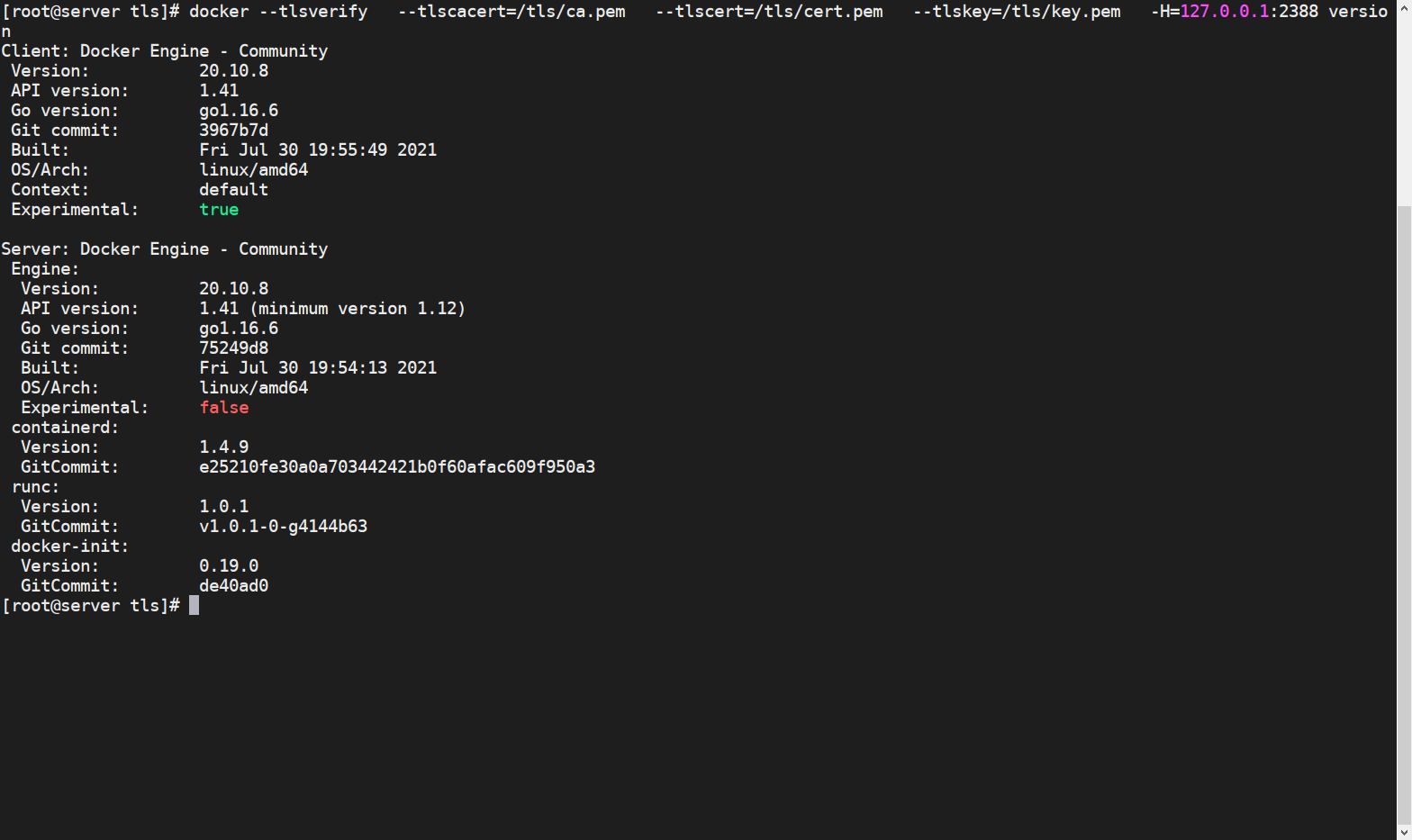
15. Client authentication
The certificate will be found under
~/.dockerby default
docker --tlsverify -H=192.168.95.132:2388 version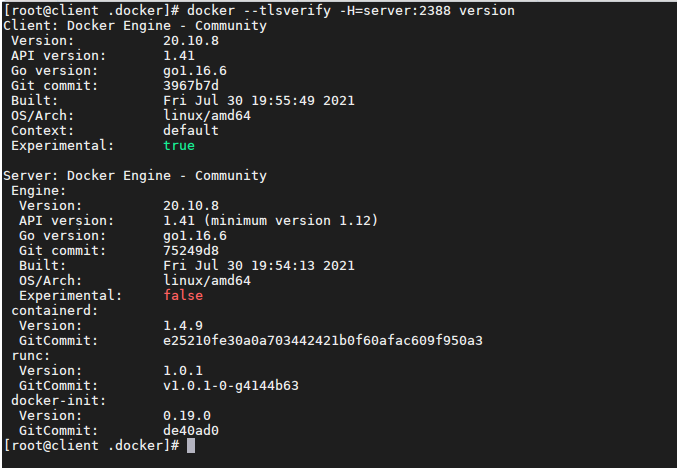


Post comment 取消回复